Python certifi provides Mozilla’s thoroughly curated collection of Root Certificates for validating the trustworthiness of SSL certificates while verifying the identity of TLS hosts. It has been plucked from the requests project.
Installing certifi package
To install the certifi package, type the following command.
python3 -m pip install certifi # OR pip install certifi
If you have installed the requests library already, there is a 100% chance that the certifi library is also installed, but you have to check it.
Installing certifi on Windows
- Type cmd in the search bar and hit Enter to open the command line.
- Type python3 -m pip install certifi in the command line and hit Enter again. This installs certifi for your default Python installation.
- The previous command may not work if you have both Python versions 2 and 3 on your computer. In that case, try the pip3 install certifi command. It is now installed in your system.
Installing certifi on Linux
- First, open the terminal or shell in your Linux OS.
- Type python3 -m pip install certifi, and hit Enter.
- If it doesn’t work, try using this command: pip3 install certifi or python -m pip install certifi.
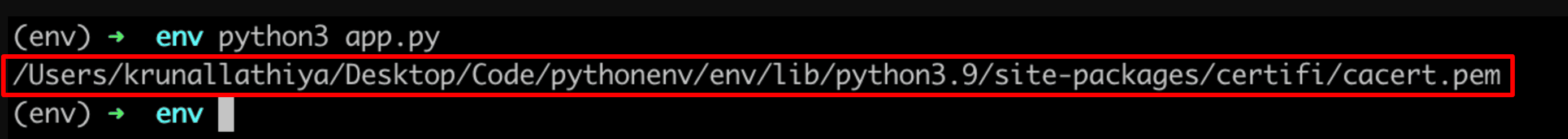
certifi.where()
The certifi.where() function helps us find the reference of the installed certificate authority (CA) bundle in Python.
import certifi print(certifi.where())
Output
You can also find the cacert.pem path from the command line using the following command.
python -m certifi /Users/krunal/Library/Python/3.8/lib/python/site-packages/certifi/cacert.pem
Browsers and certificate authorities have finalized that 1024-bit keys are unacceptably weak for certificates, particularly root certificates.
For the same reason, Mozilla has removed any weak (i.e., 1024-bit key) certificate from its bundle, replacing it with the equivalent robust (i.e., 2048-bit or higher key) certificate from the same CA.
If you put the additional certificates in the PEM bundle file, you can use these two environment variables to overwrite the default cert stores used by Python OpenSSL and Requests.
SSL_CERT_FILE=/System/Library/OpenSSL/cert.pem REQUESTS_CA_BUNDLE=/System/Library/OpenSSL/cert.pem
However, we can quickly check for this when our scripts start up and update the CA bundle automatically with a given CA if necessary.
First, capture your custom CA and save it as the PEM; you can convert it using OpenSSL.
If you only have a .cer, .crt, or .derenSSL.
openssl x509 -inform der -in certificate.cer -out certificate.pem
When you have multiple custom intermediates or roots, you can add them all into a single .pem file when converting them all.
Drag the certificate.pem into the root of your project.
Now, we’re going to try requesting the target URL. In our case, it is a GitHub API, and if we hit the cert error, update the CA bundle in use by Certifi.
import certifi
import requests
try:
print('Checking connection to Github...')
test = requests.get('https://api.github.com')
print('Connection to Github OK.')
except requests.exceptions.SSLError as err:
print('SSL Error. Adding custom certs to Certifi store...')
cafile = certifi.where()
with open('certicate.pem', 'rb') as infile:
customca = infile.read()
with open(cafile, 'ab') as outfile:
outfile.write(customca)
print('That might have worked.')Output
Checking connection to Github...
Connection to Github OK.Fixing ModuleNotFoundError: No module named “certifi”
ModuleNotFoundError: No module named “certifi” exception is raised when either the certifi module is not installed correctly, or you forgot to install the certifi package.
To fix the error, install the certifi library using “python3 -m pip install certifi” or “pip install certifi” in your operating system’s shell or terminal first.


Anil
Krunal, I really enjoyed the well explained in-depth knowledge.
Quick question: Do we need to get root & intermediate certs(base64) along with publick cert value in the .pem file?
Suvrat Rai
Hi Krunal,
Thank you for your detailed post. It was really helpful in resolving a self signed certificate error that i was getting since some time.
@Anil: Yes I would suggest that all root & intermediate certificates are taken together in the pem file.
Sameer
Can you describe something about how to resolve this error –
ssl.SSLCertVerificationError: [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: certificate has expired (_ssl.c:1129) ?
Eric Rosals
Hi Krunal, it worked and but not entirely. I downloaded the certificate and added to this file certifi.where() successfully, but still getting error on request.
Should the certificate downloaded be processed before adding the the certifi.where() file?
Thanks